- PlzHelp started following Fake 'Adobe Flash Player.dmg' malware?
Fake 'Adobe Flash Player.dmg' malware?
PlzHelp posted a topic in Mac Malware Removal Help & Support
So I was cleaning out my downloads folder when I came across an 'Adobe Flash Player.dmg', I assumed it must have just been some sort of update when I needed a flash player for something on the browser. So I opened it and when in installer window popped up I (stupidly) without even looking just double clicked on the icon which was titled 'install.command' (see pics). Terminal then opened up and ran some code, which I've saved, I'll just paste the code it ran right here. Anyone able to tell me what this did, if I need to worry about it, and if so how to get rid of it? Thanks. Last login: Sun Nov 18 16:18:14 on ttys000 MacBook-Pro:~ scotty$ /Volumes/Install/Install.command ; exit; x ./mm-install-macos.app/ x ./mm-install-macos.app/Contents/ x ./mm-install-macos.app/Contents/_CodeSignature/ x ./mm-install-macos.app/Contents/Info.plist x ./mm-install-macos.app/Contents/MacOS/ x ./mm-install-macos.app/Contents/PkgInfo x ./mm-install-macos.app/Contents/Resources/ x ./mm-install-macos.app/Contents/Resources/__TBT_RequestForm.nib x ./mm-install-macos.app/Contents/Resources/__TBT_Template_Base.nib x ./mm-install-macos.app/Contents/Resources/locked.icns x ./mm-install-macos.app/Contents/Resources/MainWindow.nib x ./mm-install-macos.app/Contents/Resources/mm-install-macos.icns x ./mm-install-macos.app/Contents/MacOS/mm-install-macos x ./mm-install-macos.app/Contents/_CodeSignature/CodeResources 2018-11-22 00:10:51.312 mm-install-macos[52068:11813830] __tbt_findStubPath PPID: 52040 2018-11-22 00:10:51.312 mm-install-macos[52068:11813830] __tbt_findStubPath CMD: ps -wwo args 52040 | tail -1 | sed -nE 's/(/bin/bash[ ]?)([^ ]+).*/2/p' 2018-11-22 00:10:51.535 mm-install-macos[52068:11813830] __tbt_findStubPath fullPath: /Volumes/Install/Install.command 2018-11-22 00:10:51.535 mm-install-macos[52068:11813830] __tbt_getMountingPoint originalPath (1): /Volumes/Install/Install.command 2018-11-22 00:10:51.535 mm-install-macos[52068:11813830] __tbt_getMountingPoint originalPath (2): /Volumes/Install/Install.command 2018-11-22 00:10:51.535 mm-install-macos[52068:11813830] __tbt_getMountingPoint mountingPoint (1): /Volumes/Install 2018-11-22 00:10:51.535 mm-install-macos[52068:11813830] __tbt_getMountingPoint mountingPoint (2): /Volumes/Install 2018-11-22 00:10:51.800 mm-install-macos[52068:11813830] __tbt_getDmgSourcePathByMountingPoint mountingPoint=/Volumes/Install plistData=<3c3f786d 6c207665 7273696f 6e3d2231 2e302220 656e636f 64696e67 3d225554 462d3822 3f3e0a3c 21444f43 54595045 20706c69 73742050 55424c49 4320222d 2f2f4170 706c652f 2f445444 20504c49 53542031 2e302f2f 454e2220 22687474 703a2f2f 7777772e 6170706c 652e636f 6d2f4454 44732f50 726f7065 7274794c 6973742d 312e302e 64746422 3e0a3c70 6c697374 20766572 73696f6e 3d22312e 30223e0a 3c646963 743e0a09 3c6b6579 3e667261 6d65776f 726b3c2f 6b65793e 0a093c73 7472696e 673e3438 302e3630 2e313c2f 73747269 6e673e0a 093c6b65 793e696d 61676573 3c2f6b65 793e0a09 3c617272 61793e0a 09093c64 6963743e 0a090909 3c6b6579 3e617574 6f646973 6b6d6f75 6e743c2f 6b65793e 0a090909 3c747275 652f3e0a 0909093c 6b65793e 626c6f63 6b636f75 6e743c2f 6b65793e 0a090909 3c696e74 65676572 3e323034 38303c2f 696e7465 6765723e 0a090909 3c6b6579 3e626c6f 636b7369 7a653c2f 6b65793e 0a090909 3c696e74 65676572 3e353132 3c2f696e 74656765 723e0a09 09093c6b 65793e68 6469642d 7069643c 2f6b6579 3e0a0909 093c696e 74656765 723e3532 3031383c 2f696e74 65676572 3e0a0909 093c6b65 793e6963 6f6e2d70 6174683c 2f6b6579 3e0a0909 093c7374 72696e67 3e2f5379 7374656d 2f4c6962 72617279 2f507269 76617465 4672616d 65776f72 6b732f44 69736b49 6d616765 732e6672 616d6577 6f726b2f 5265736f 75726365 732f4344 69736b49 6d616765 2e69636e 733c2f73 7472696e 673e0a09 09093c6b 65793e69 6d616765 2d616c69 61733c2f 6b65793e 0a090909 3c646174 613e0a09 09094141 41414141 47674141 49414141 784e5957 4e70626e 52766332 67675345 51414141 41414141 41414141 41414141 41414141 44550a09 09096a6f 536d5343 73414141 41486b30 30575157 5276596d 5567526d 78686332 67675547 78686557 56794c6d 52745a77 41414141 41410a09 09094141 41414141 41414141 41414141 41414141 41414141 41414141 41414141 41414141 41414141 41414141 41414141 41414144 69300a09 09093764 67583078 51414141 41414141 41414150 2f2f2f2f 38414141 6b674141 41414141 41414141 41414141 41414141 41414355 52760a09 09096432 35736232 466b6377 41414541 41494141 44556a66 67474141 41414551 41494141 44594630 5a304141 41414151 414d4141 65540a09 09095451 41486b30 6f41426d 6c4f4141 49415055 31685932 6c756447 397a6143 42495244 70566332 5679637a 6f416332 4e766448 52350a09 09094f67 42456233 64756247 39685a48 4d364145 466b6232 4a6c4945 5a735958 4e6f4946 42735958 6c6c6369 356b6257 63414141 34410a09 09094c67 41574145 45415a41 42764147 49415a51 41674145 59416241 42684148 4d416141 41674146 41416241 42684148 6b415a51 42790a09 09094143 34415a41 42744147 63414477 41614141 77415451 42684147 4d416151 42754148 51416277 427a4147 67414941 42494145 51410a09 09094567 41745658 4e6c636e 4d766332 4e766448 52354c30 52766432 35736232 466b6379 39425a47 39695a53 42476247 467a6143 42510a09 09096247 46355a58 49755a47 316e4141 41544141 45764141 41564141 49414466 2f2f4141 413d0a09 09093c2f 64617461 3e0a0909 093c6b65 793e696d 6167652d 656e6372 79707465 643c2f6b 65793e0a 0909093c 66616c73 652f3e0a 0909093c 6b65793e 696d6167 652d7061 74683c2f 6b65793e 0a090909 3c737472 696e673e 2f557365 72732f73 636f7474 792f446f 776e6c6f 6164732f 41646f62 6520466c 61736820 506c6179 65722e64 6d673c2f 73747269 6e673e0a 0909093c 6b65793e 696d6167 652d7479 70653c2f 6b65793e 0a090909 3c737472 696e673e 55444946 20726561 642d6f6e 6c792063 6f6d7072 65737365 64202862 7a697032 293c2f73 7472696e 673e0a09 09093c6b 65793e6f 776e6572 2d756964 3c2f6b65 793e0a09 09093c69 6e746567 65723e35 30313c2f 696e7465 6765723e 0a090909 3c6b6579 3e72656d 6f766162 6c653c2f 6b65793e 0a090909 3c747275 652f3e0a 0909093c 6b65793e 73797374 656d2d65 6e746974 6965733c 2f6b6579 3e0a0909 093c6172 7261793e 0a090909 093c6469 63743e0a 09090909 093c6b65 793e636f 6e74656e 742d6869 6e743c2f 6b65793e 0a090909 09093c73 7472696e 673e4755 49445f70 61727469 74696f6e 5f736368 656d653c 2f737472 696e673e 0a090909 09093c6b 65793e64 65762d65 6e747279 3c2f6b65 793e0a09 09090909 3c737472 696e673e 2f646576 2f646973 6b323c2f 73747269 6e673e0a 09090909 3c2f6469 63743e0a 09090909 3c646963 743e0a09 09090909 3c6b6579 3e636f6e 74656e74 2d68696e 743c2f6b 65793e0a 09090909 093c7374 72696e67 3e343834 36353330 302d3030 30302d31 3141412d 41413131 2d303033 30363534 33454341 433c2f73 7472696e 673e0a09 09090909 3c6b6579 3e646576 2d656e74 72793c2f 6b65793e 0a090909 09093c73 7472696e 673e2f64 65762f64 69736b32 73313c2f 73747269 6e673e0a 09090909 093c6b65 793e6d6f 756e742d 706f696e 743c2f6b 65793e0a 09090909 093c7374 72696e67 3e2f566f 6c756d65 732f496e 7374616c 6c3c2f73 7472696e 673e0a09 0909093c 2f646963 743e0a09 09093c2f 61727261 793e0a09 09093c6b 65793e77 72697465 61626c65 3c2f6b65 793e0a09 09093c66 616c7365 2f3e0a09 093c2f64 6963743e 0a093c2f 61727261 793e0a09 3c6b6579 3e726576 6973696f 6e3c2f6b 65793e0a 093c7374 72696e67 3e31302e 31337634 38302e36 302e313c 2f737472 696e673e 0a093c6b 65793e76 656e646f 723c2f6b 65793e0a 093c7374 72696e67 3e417070 6c653c2f 73747269 6e673e0a 3c2f6469 63743e0a 3c2f706c 6973743e 0a> 2018-11-22 00:10:51.801 mm-install-macos[52068:11813830] __tbt_getDmgSourcePathByMountingPoint imageSourcePath=/Users/scotty/Downloads/Adobe Flash Player.dmg 2018-11-22 00:10:51.801 mm-install-macos[52068:11813830] __tbt_getInjectedParams dmgSourcePath: /Users/scotty/Downloads/Adobe Flash Player.dmg 2018-11-22 00:10:51.830 mm-install-macos[52068:11813830] __tbt_getInjectedParams :: kMDItemWhereFroms: ( ', ' ) 2018-11-22 00:10:51.830 mm-install-macos[52068:11813830] __tbt_getInjectedParams :: URL: 2018-11-22 00:10:51.830 mm-install-macos[52068:11813830] __tbt_getInjectedParams :: URL: 2018-11-22 00:10:51.830 mm-install-macos[52068:11813830] __tbt_getInjectedParams injected params: 2018-11-22 00:10:56.922 defaults[52074:11813887] No domain, key, nor value containing 'SearchQuick' ls: /Users/scotty/Library/Application Support/Firefox/Profiles/: No such file or directory 2018-11-22 00:10:57.149 defaults[52080:11813949] No domain, key, nor value containing 'search-quick' ls: /Users/scotty/Library/Application Support/Firefox/Profiles/: No such file or directory logout Saving session... ...copying shared history... ...saving history...truncating history files... ...completed. Deleting expired sessions...11 completed. [Process completed]
- Mac Media Player Update Virus
- Flash Player Dmg Virus Removal Download
- Flash Player Dmg Virus Removal Free
- Flash Player Dmg Virus Removal Tool
- Flash Player.dmg Virus Removal Mac
A decade-old Windows malware trojan wormed its way into the macOS ecosystem, complete with a signed (likely stolen) Apple developer certificate. The exploit appears as an Adobe Flash Player installer. Once permission is granted, it hides itself deep inside macOS folders. Its certificate has already been revoked by Apple, but it's good to be aware of your enemies.
Fake Adobe Flash Player installer: Another screenshot of fake Adobe Flash Player installer: Instant automatic Mac malware removal: Manual threat removal might be a lengthy and complicated process that requires advanced computer skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of Mac malware. Apr 25, 2018 PSA: There’s a new fake Flash Player installer for Macs, and it’s nastier than usual. Usually, software like Malwarebytes can search for and remove malware automatically. Malware + Recommended + Security News. Fake Flash Player Update Infects Macs with Scareware Updated Posted on February 5th, 2016 by Graham Cluley Anyone who has been using computers for any length of time should (hopefully) be aware of the endless ritual of updating Adobe Flash. “Flash Player Update Download New Version” Redirect Pop-up Removal Guide (Mac) Why the “Flash Player Update Download New Version” site appears on the Safari, Chrome or Mozilla browsers? Beware of “Flash Player Update Download New Version” pop-ups that appear unexpectedly while surfing or unknowingly from any redirect link. Dec 04, 2018 I was on a streaming music website and received a popup talking about Adobe Flash player, so I closed the window but it already had downloaded 'Adobe Flash Player.dmg' in that time. I meant to click the menu button (three dots) on the file at the bottom bar of my chrome to delete it, but I accidentally clicked the border and inadvertently.
According to Fox-IT, Snake, a malware framework that has been infecting Windows software since 2008, and more recently Linux, is now targeting Mac.
Now, Fox-IT has identified a version of Snake targeting Mac OS X.As this version contains debug functionalities and was signed on February 21st, 2017 it is likely that the OS X version of Snake is not yet operational.Fox-IT expects that the attackers using Snake will soon use the Mac OS X variant on targets.
Snakes are dangerous and here's why
Similar to the Dok trojan that we heard about earlier this week, Snake popped up with an authenticated developer certificate, which means the Mac's built-in security system, Gatekeeper, would consider it legit and allow the installation process to complete.
It's important to note that Apple has already revoked this fake or stolen developer certificate, so Gatekeeper will block it. However, there is still a slight chance of someone downloading Snake by accident if they've found it through dubious channels. Malwarebytes explains:
Fortunately, Apple revoked the certificate very quickly, so this particular installer is no further danger unless the user is tricked into downloading it via a method that doesn't mark it with a quarantine flag (such as via most torrent apps).
How Snake slithers into your Mac
Just like most malware attacks, Snake doesn't just magically appear on your Mac one day. There isn't someone shooting corrupted files through your ethernet cable directly into your software. Snake has to be welcomed into your operating system by you.
Think of it is a vampire. If you don't invite it into your home, it can't attack you.
The file, named Install Adobe Flash Player.app.zip, will appear to be an Adobe Flash installer (Say what you will about Flash, but there are still a lot of people that have to use it for school or work). From Malwarebytes:
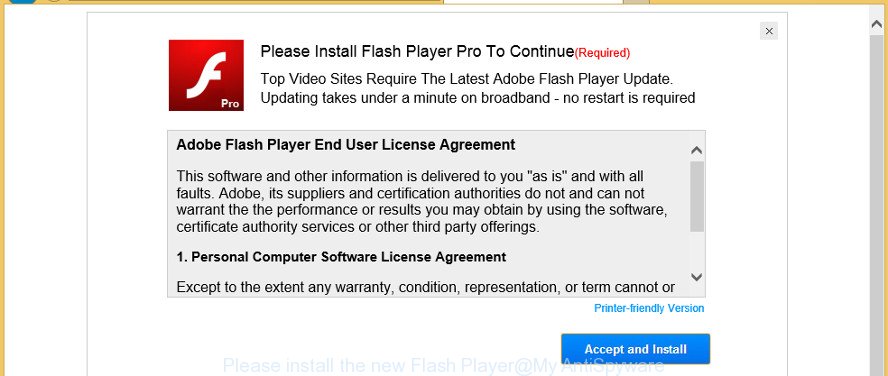
If the app is opened, it will immediately ask for an admin user password, which is typical behavior for a real Flash installer. If such a password is provided, the behavior continues to be consistent with the real thing.
Interestingly, once the installation is complete, Flash is actually installed on the Mac, making it even more difficult to tell that it's a trojan.
Mac Media Player Update Virus
How you can protect yourself against Snake
As noted above, the fake/stolen developer certificate that allowed Snake to get a pass from Gatekeeper has already been revoked, so it's likely that, even if you download the zip file and try to open the app, your built-in security program will say, 'Nope Dope!'
But to refresh best practices, if you receive an email with an attachment at all, do some due diligence to make sure it's from a legitimate source. Check the sender address to make sure it is from an address you recognize. Click on the sender's name to view the email address it was sent from to make sure it's not a spoofed email. If you're still unsure, confirm with the sender by texting, calling or sending a separate email asking if the attachment is legit.
Specific to the Snake trojan, avoid downloading any zip files with the name Install Adobe Flash Player.app.zip.
Flash Player Dmg Virus Removal Download
What to do if Snake already bit you
Do you like my snake puns?
If you think you might have managed to accidentally install the Snake trojan onto your Mac, you can find and delete the following files:
- /Library/LaunchDaemons/com.adobe.update.plist
- /Library/Scripts/installd.sh
- /Library/Scripts/queue
- /var/tmp/.ur-*
- /tmp/.gdm-socket
- /tmp/.gdm-selinux
Next, delete the stolen/fake signed Apple Developer certificate.
Flash Player Dmg Virus Removal Free
- Launch Finder.
- Select Applications.
- Open your Utilities folder.
- Double-click on Keychain Access.
- Select the certificate named Adobe Flash Player installer with the signed certificate issued to Addy Symonds.
- Right or Control + click on the Certificate.
- Select Delete Certificate from the drop down options.
- Select Delete to confirm that you want to delete the certificate.
Lastly, change your administrator password to ensure that you're backdoor is rekeyed so the hackers can't get back in.
Remember best practices for staying safe
It is unlikely, at this point, that Snake will slither through your Mac's backdoor. For one, Apple has revoked the certificate, which makes it nearly impossible to make it through the installation process without you knowing about it.
To reiterate, don't open attachments from unknown sources. Double check the sender email address to make sure it is not spoofed. Don't open suspicious-looking files or give administrator permission to unknown programs. You can protect yourself from attacks if you stay safe.
If you do end up with malware on your Mac, take a moment to relax and know that everything will be O.K. You can remove malware on your own, but if it seems too difficult for you to tackle, you can talk to Apple support. Someone will be able to help you.
MacBook Pro
Main
Flash Player Dmg Virus Removal Tool
How low can you go?Flash Player.dmg Virus Removal Mac
Stores run out of iPhone 11 stock as coronavirus stranglehold continues
If you're in New York City and want an iPhone 11 or iPhone 11 Pro, you're probably out of luck.